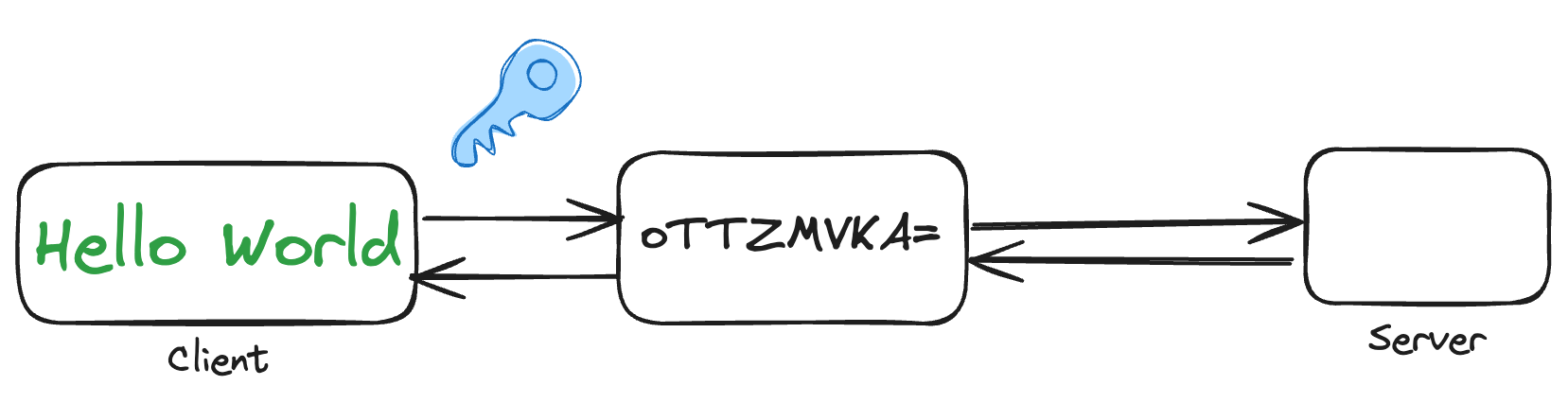
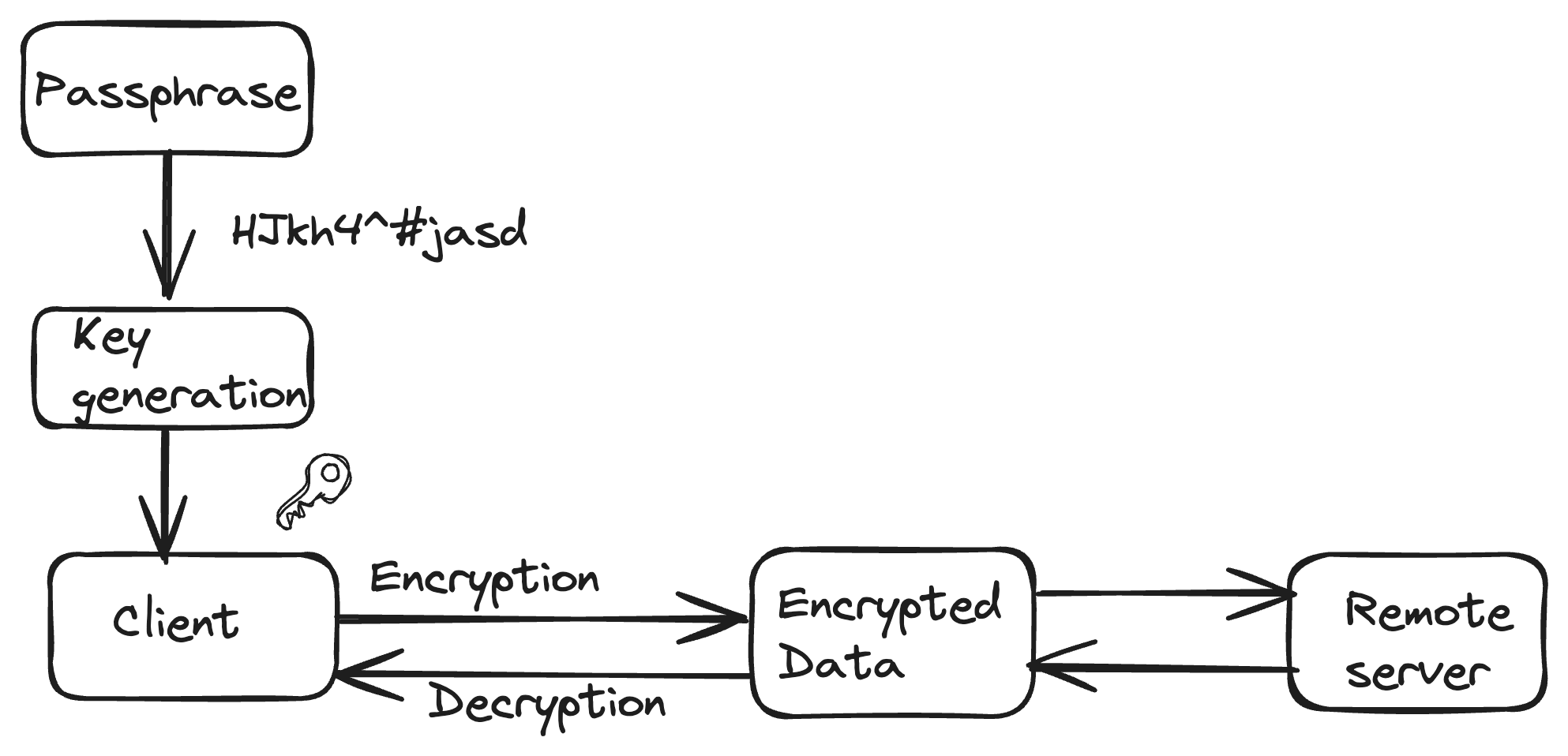
Tigris being S3 compatible, offers S3-supported authentication and authorization methods. AWS S3 evolved in offerings for their authentication and authorization needs. We support what AWS S3 recommends to their users as of now for the AuthN and AuthZ needs.